Security researchers have revealed a new mobile spyware platform called ZeroDayRAT, which is being promoted on Telegram as a tool for harvesting sensitive information and enabling real-time monitoring on Android and iOS devices.
According to Daniel Kelley, a security researcher at iVerify, the developer operates dedicated Telegram channels for sales, support, and updates, providing buyers with a centralized gateway to a fully functional spyware control panel. Kelley noted that the platform surpasses ordinary data collection, extending into live surveillance and direct financial theft. ZeroDayRAT supports Android 5 through 16 and iOS versions up to 26. The malware is believed to spread via social engineering tactics and fraudulent app marketplaces. Buyers receive a builder to generate malicious binaries and an online management panel they can deploy on their own servers.
After a device is compromised, operators can view comprehensive device details via a self-hosted dashboard model, location, OS version, battery level, SIM and carrier information, app usage, notifications, and even previews of recent SMS messages. These insights help attackers profile victims, identify contacts, and determine the most-used apps. The panel also collects current GPS coordinates and displays them on Google Maps, while maintaining a historical location trail, effectively functioning as full-fledged spyware. Kelley highlighted the accounts section as particularly concerning: it enumerates every account configured on the device Google, WhatsApp, Instagram, Facebook, Telegram, Amazon, Flipkart, PhonePe, Paytm, Spotify, and others—along with associated usernames or email addresses.
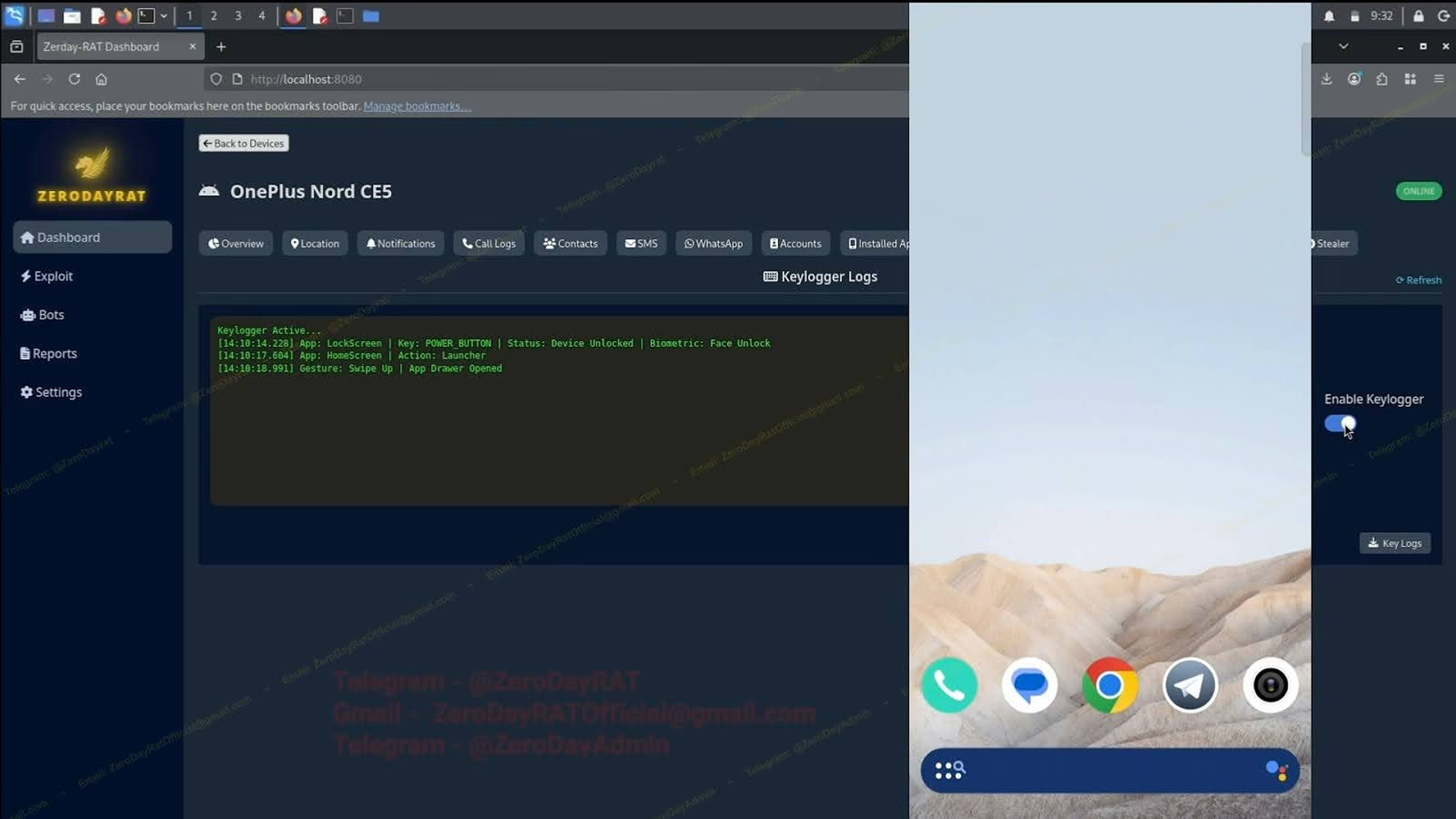
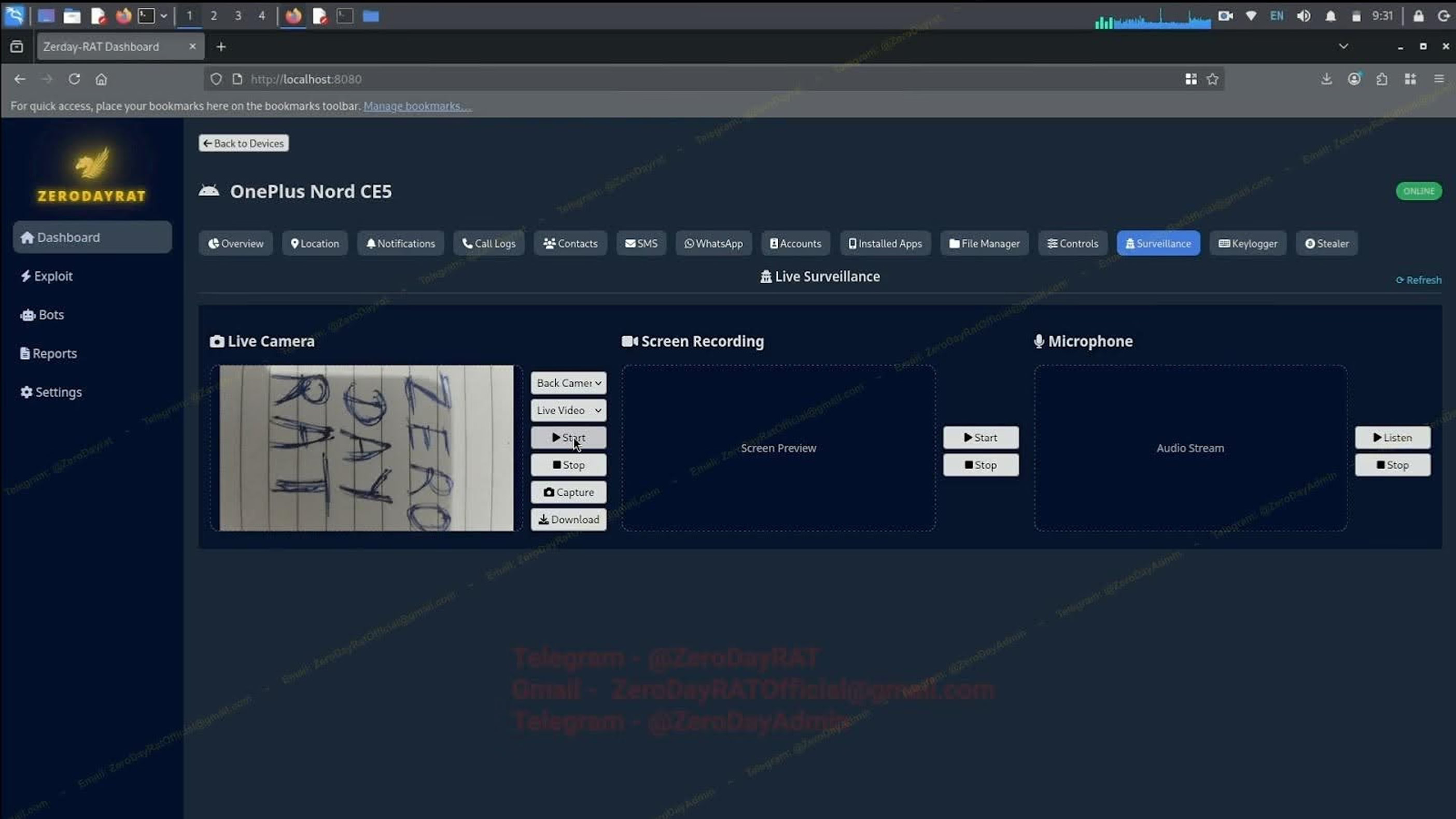
Additional features include keylogging, collection of SMS messages (including one-time passwords used for 2FA bypass), and interactive control such as live camera streaming and microphone access to facilitate remote eavesdropping. For financial theft, ZeroDayRAT integrates a stealer that scans for crypto wallet apps MetaMask, Trust Wallet, Binance, Coinbase—and replaces wallet addresses copied to the clipboard, diverting funds to attacker-controlled wallets. A separate banking stealer module targets Apple Pay, Google Pay, PayPal, and PhonePe, the latter leveraging India’s UPI protocol for peer-to-peer and merchant transactions. “Taken together,” Kelley said, this is a complete mobile compromise suite—capabilities once requiring nation-state resources or custom exploit development now marketed on Telegram. A single customer can obtain location, messages, financial data, camera/mic feeds, and keystrokes from a browser tab. With cross-platform coverage and active development, the threat surface for both individuals and organizations is expanding.
ZeroDayRAT’s tactics mirror those of many mobile threats that spread via phishing or by slipping into official app stores. Over recent years, adversaries have continually found ways to evade Apple and Google safeguards and convince users to install malicious software. On iOS, attackers frequently abuse enterprise provisioning intended for internal app deployment without App Store publication. Toolkits that blend spyware, surveillance, and info-stealing functions reduce the skill required to conduct attacks and underscore the growing sophistication and persistence of mobile-focused cybercrime.
This commercialization trend surfaces alongside a wave of recent mobile malware and scams:
- Android RATs hosted on Hugging Face: Campaigns have distributed malicious APKs via dropper apps (e.g., TrustBastion). After installation, users are prompted to “update,” which pulls the payload from Hugging Face. The malware then requests accessibility and other sensitive permissions to enable surveillance and credential theft.
- Arsink Android RAT: Uses Google Apps Script to exfiltrate media/files to Google Drive, and relies on Firebase and Telegram for C2. Distributed through Telegram, Discord, and MediaFire, often impersonating popular brands. Infections have clustered in Egypt, Indonesia, Iraq, Yemen, and Türkiye.
- All Document Reader (package: com.recursivestd.highlogic.stellargrid) on Google Play: Flagged as an installer for the Anatsa/TeaBot/Toddler banking trojan. Accrued 50,000+ downloads before removal.
- deVixor banking trojan: Targeting Iranian users since October 2025 via phishing sites spoofing legitimate automotive businesses. Besides data theft, it includes a remotely triggered ransomware function to lock devices and demand cryptocurrency. Uses Google Firebase for commands and Telegram bots for administration.
- ShadowRemit: Employs fake Android apps and Google Play lookalike pages to facilitate unlicensed cross-border remittances. Victims are told to send funds to beneficiary accounts/e-wallets and submit transaction screenshots for “verification,” a pattern consistent with money mule collection workflows.
- India-focused Android malware: Abuses the credibility of government services and official digital platforms to propagate malicious APKs via WhatsApp, enabling data theft, persistence, and even crypto-mining.
- Triada operators: Use phishing pages masquerading as Chrome updates to deliver APKs hosted on GitHub. Analysts report attackers are commandeering long-standing, verified advertiser accounts to drive malicious redirects.
- WhatsApp-centric scams: Fraudsters use video calls, posing as bank or Meta support staff, then coerce victims into screen sharing and installing legitimate remote access tools like AnyDesk or TeamViewer to exfiltrate sensitive data.
- GhostChat spyware (Pakistan): Distributed through romance scam lures via a bogus dating app, GhostChat, to siphon victim data. The same actors are suspected of running ClickFix (DLL payloads for system reconnaissance and remote command execution) and a WhatsApp device-linking scheme dubbed GhostPairing to seize account access.
- Phantom click-fraud trojans: Leverage TensorFlow.js to automatically detect and interact with ads in a hidden WebView. A WebRTC “signaling” mode streams a live feed of the virtual browser, letting attackers click, scroll, and type remotely. Spread via mobile games on Xiaomi’s GetApps and other unofficial stores.
- NFCShare malware**:** Delivered through a Deutsche Bank phishing campaign as “deutsche.apk” under the guise of an update, it reads NFC card data and exfiltrates via WebSocket. It resembles NFC relay families such as NGate, ZNFC, SuperCard X, PhantomCard, and RelayNFC, with related C2 infrastructure previously tied to SuperCard X in November 2025.
A report last month from Group-IB highlights a surge in NFC-enabled Android tap-to-pay malware, commonly advertised in Chinese cybercrime communities on Telegram. The NFC relay method—also known as Ghost Tap is central to these schemes. Group-IB documented at least $355,000 in fraudulent transactions from a single POS vendor between November 2024 and August 2025. In another observed pattern, mules used mobile wallets preloaded with compromised cards to make purchases worldwide.
The firm identified three prominent vendors of Android NFC relay apps TX-NFC, X-NFC, and NFU Pay. TX-NFC has amassed 25,000+ Telegram subscribers since early January 2025, while X-NFC and NFU Pay have 5,000+ and 600+ subscribers, respectively. These attacks aim to trick victims into installing NFC-capable malware and tapping their physical payment cards against their phones. The captured transaction data is then relayed to an attacker device via an adversary-operated server. A dedicated app on the money mule’s device completes payments or cash-outs as if the victim’s card were physically present.
Calling tap-to-pay fraud a growing threat, Group-IB observed a steady rise in malware detections from May 2024 through December 2025. New families and variants continue to appear while older strains remain active—evidence of the widening adoption of these techniques among cybercriminals.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



