DPRK IT Operatives Intensify LinkedIn Impersonation to Secure Remote Jobs
Information technology (IT) workers linked to the Democratic People’s Republic of Korea (DPRK) are increasingly applying for remote roles using real LinkedIn accounts belonging to people they’re impersonating an escalation of an already well‑established fraud scheme.
According to Security Alliance (SEAL), these hijacked or co‑opted profiles often display verified workplace emails and identity badges, a tactic designed to lend credibility and make fraudulent job applications appear authentic.
The Long-Running “DPRK IT Worker” Operation
This campaign tracked by the wider security community as Jasper Sleet, PurpleDelta, and Wagemole involves DPRK operatives posing as remote professionals under stolen or fabricated identities to gain employment at Western and other international companies.
Objectives are twofold:
- Generate steady income to support national weapons programs.
- Enable espionage by stealing sensitive data; in some cases, operators escalate to extortion, threatening to leak information unless paid.
In July 2025, Silent Push described the program as a “high‑volume revenue engine” that also grants adversaries administrative access to sensitive codebases and allows living‑off‑the‑land persistence in corporate environments.
Chainalysis reported in October 2025 that once salaries are received, DPRK IT workers launder cryptocurrency using techniques such as chain‑hopping and token swapping, leveraging smart contracts, decentralized exchanges, and bridge protocols to obscure fund flows on‑chain.
Defensive Guidance for Potential Victims of Identity Misuse
Individuals who suspect their identities are being used in fraudulent applications should consider:
- Posting a public warning on social media.
- Listing official communication channels and a verification method (e.g., corporate email).
- Ensuring recruiters validate account ownership for example, by asking candidates to connect on LinkedIn using the email they provided or to confirm control through an authenticated channel.
SEAL emphasizes simple checks to confirm that the same person controls both the email and the LinkedIn account.
National Warnings and Business Impact
The Norwegian Police Security Service (PST) recently warned of multiple cases in the past year where Norwegian firms unwittingly hired likely North Korean IT workers for home‑based roles. PST assessed that wages from such employment likely fund the country’s weapons and nuclear programs.
Parallel Social Engineering: “Contagious Interview”
Alongside the IT worker ruse, a related social engineering campaign dubbed Contagious Interview uses fake hiring pipelines to lure targets into interviews after first approaching them on LinkedIn. The attack escalates when supposed recruiters or hiring managers instruct applicants to complete a skills assessment that culminates in malicious code execution.
- In one case imitating a hiring flow resembling Fireblocks (a digital asset infrastructure firm), candidates were told to clone a GitHub repo and install an npm package, which ultimately triggered malware.
- The campaign has also used EtherHiding, a technique that stores and retrieves command‑and‑control (C2) elements via blockchain smart contracts, increasing resilience to takedowns (per researcher Ori Hershko).
Recent variants observed by Abstract Security and OpenSourceMalware delivered JavaScript malware disguised as web fonts using malicious Microsoft VS Code task files, resulting in the deployment of BeaverTail and InvisibleFerret for persistence and theft of crypto wallets and browser credentials.
Another branch, documented by Panther, leverages malicious npm packages to deliver a modular JavaScript remote access trojan (RAT) named Koalemos via a loader. Koalemos enters a beacon loop to:
- Fetch tasks from an external server,
- Execute them,
- Return encrypted results,
- Then sleep for a randomized interval before repeating.
Supported capabilities (12 commands) include filesystem operations, file transfer, environment discovery (e.g., whoami), and arbitrary code execution.
Packages linked to this activity include:

Per researcher Alessandra Rizzo, the initial loader performs DNS-based execution gating and engagement date checks before downloading and launching the RAT as a detached process. Koalemos then performs system fingerprinting, establishes encrypted C2, and enables full remote access.
Labyrinth Chollima: Splintering and Specialization
Meanwhile, CrowdStrike reports that the prolific North Korean threat actor Labyrinth Chollima has evolved into three distinct clusters, each with unique missions and tradecraft:
- Labyrinth Chollima (core) – Espionage-focused; known to use the FudModule rootkit for stealth and linked to Operation Dream Job, a job‑themed malware delivery operation for intelligence collection.
- Golden Chollima (aka AppleJeus, Citrine Sleet, UNC4736) – Conducts steady, smaller‑scale cryptocurrency thefts in developed markets.
- Pressure Chollima (aka Jade Sleet, TraderTraitor, UNC4899) – Targets high‑value crypto heists, deploying advanced implants against organizations with substantial digital asset exposure.
Assessments from DTEX note that Labyrinth Chollima, Andariel, and BlueNoroff are sub‑clusters within the broader Lazarus Group (aka Diamond Sleet, Hidden Cobra), with BlueNoroff further splitting into TraderTraitor and CryptoCore (aka Sapphire Sleet).
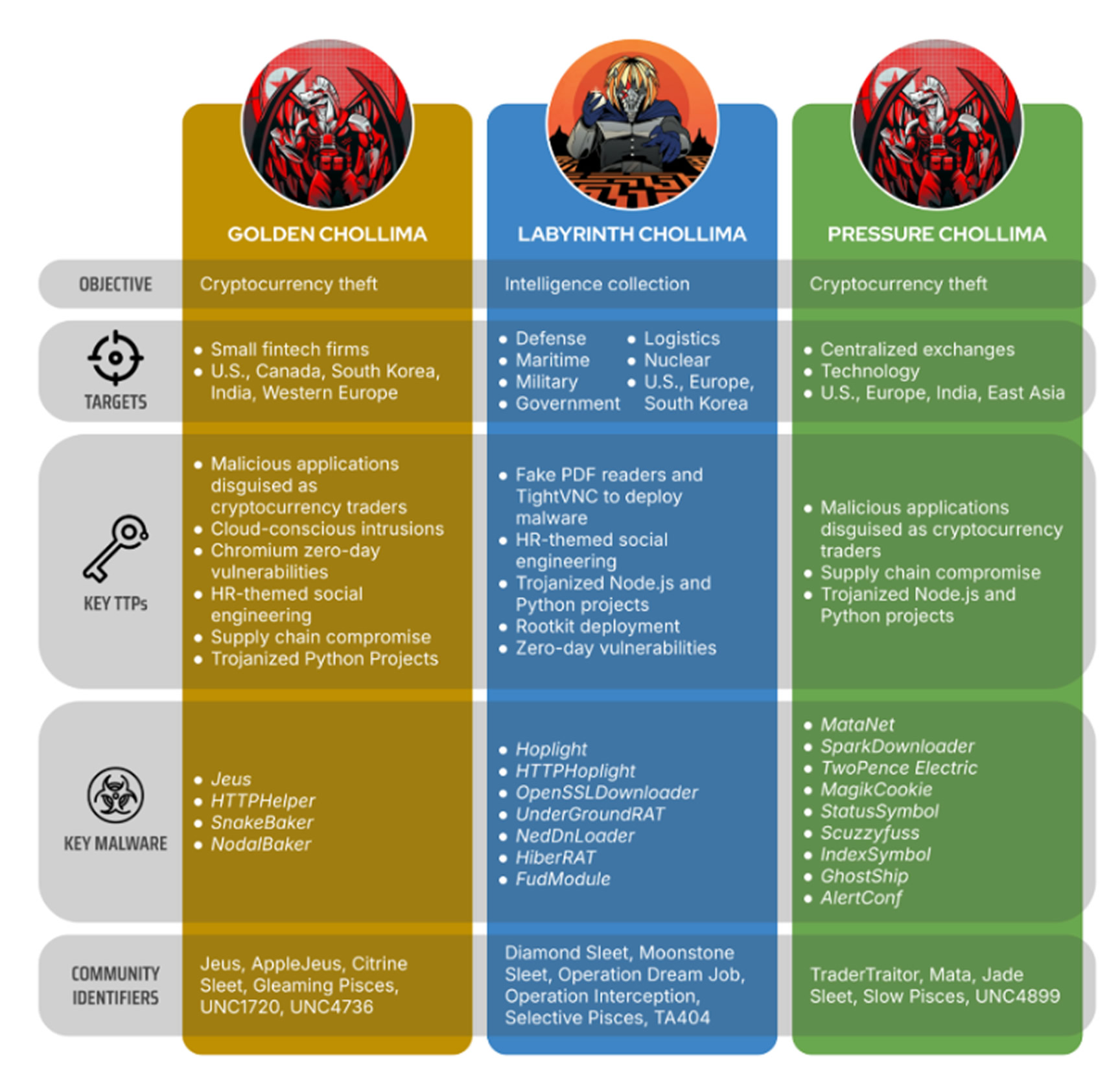
Despite the split, these actors share tools and infrastructure, signaling centralized coordination within the DPRK cyber ecosystem. As CrowdStrike puts it, they exhibit strikingly similar tradecraft including supply chain compromises, HR‑themed social engineering, trojanized legitimate software, and malicious Node.js/Python packages with significant cross‑pollination of techniques and resources.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



