A new self-propagating malware, dubbed SORVEPOTEL by Trend Micro, is rapidly spreading across Windows systems by exploiting the trust inherent in the popular messaging app, WhatsApp. This targeted campaign is heavily focused on Brazilian users.
Attack Mechanism and Propagation
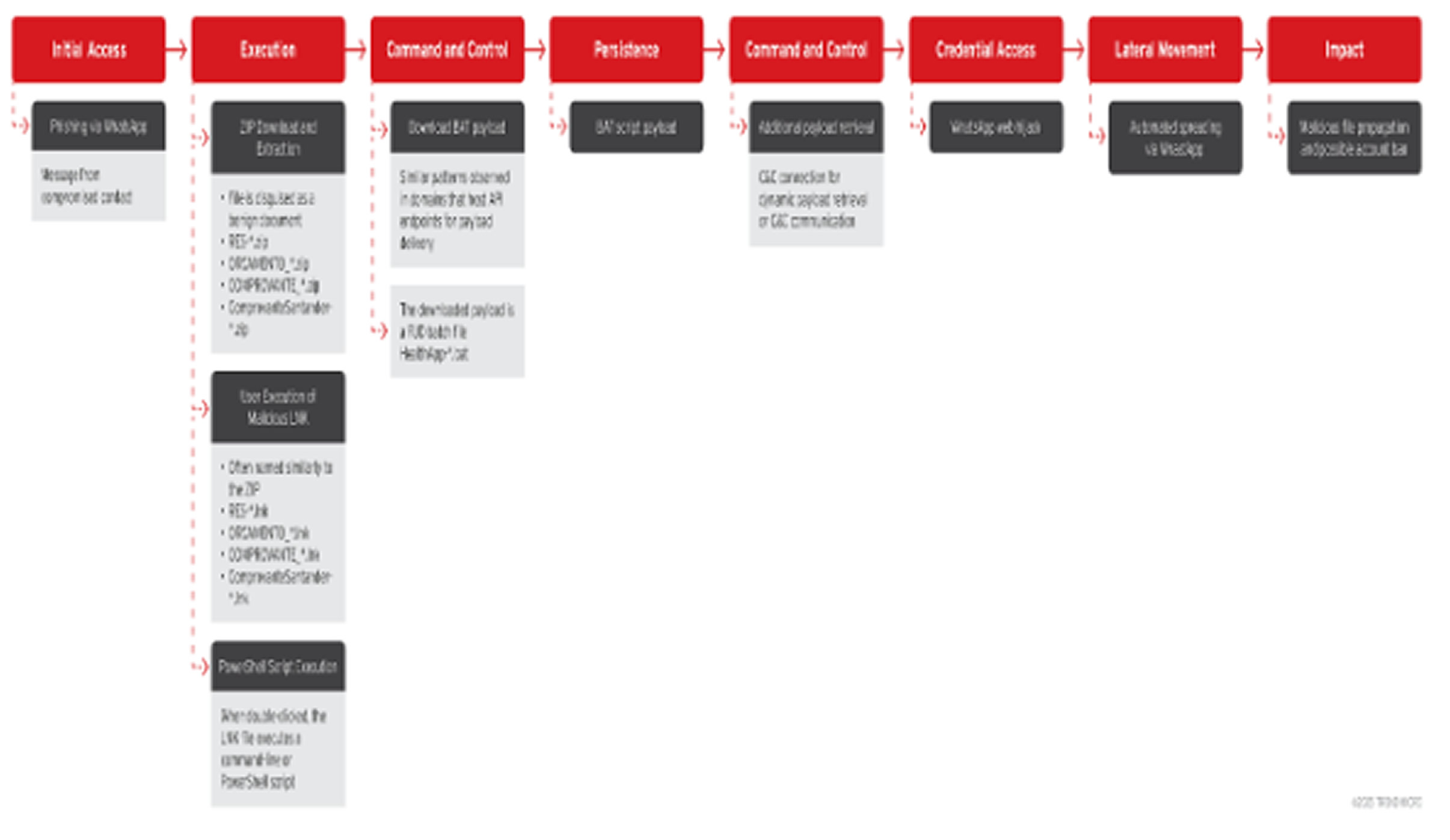
The SORVEPOTEL campaign is "engineered for speed and propagation" rather than for data theft or ransomware. It begins with a phishing message sent from a compromised contact, which gives the message a deceptive air of credibility. The message includes a malicious ZIP file disguised as a receipt or a health app document.
Since the message instructs users to open the attachment on a desktop, researchers believe the attackers are primarily targeting enterprises rather than consumers.
Here is how the attack unfolds:
Initial Compromise If the victim opens the ZIP attachment, they are tricked into launching a Windows shortcut (.LNK) file.
Payload Delivery This LNK file silently executes a PowerShell script that retrieves the main payload from an external server (e.g., sorvetenopoate.com).
Persistence The downloaded payload is a batch script that copies itself to the Windows Startup folder to ensure it automatically launches every time the system starts.
WhatsApp Spread If the malware detects that WhatsApp Web is active on the infected system, it automatically distributes the malicious ZIP file to all contacts and groups associated with the victim's account, allowing it to spread quickly and widely.
This automated spamming often results in the infected accounts being suspended or banned by WhatsApp for violating terms of service.
Geographic and Sector Impact
The vast majority of infections—457 out of 477 observed cases—are concentrated in Brazil. The most impacted sectors include government, public service, manufacturing, technology, education, and construction.
While there is some evidence the attackers also used email for distribution, the core of the SORVEPOTEL campaign demonstrates how threat actors are effectively leveraging platforms like WhatsApp to achieve rapid, large-scale malware propagation with minimal user effort. There are no indications the attackers are currently using the access to steal data or encrypt files.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



