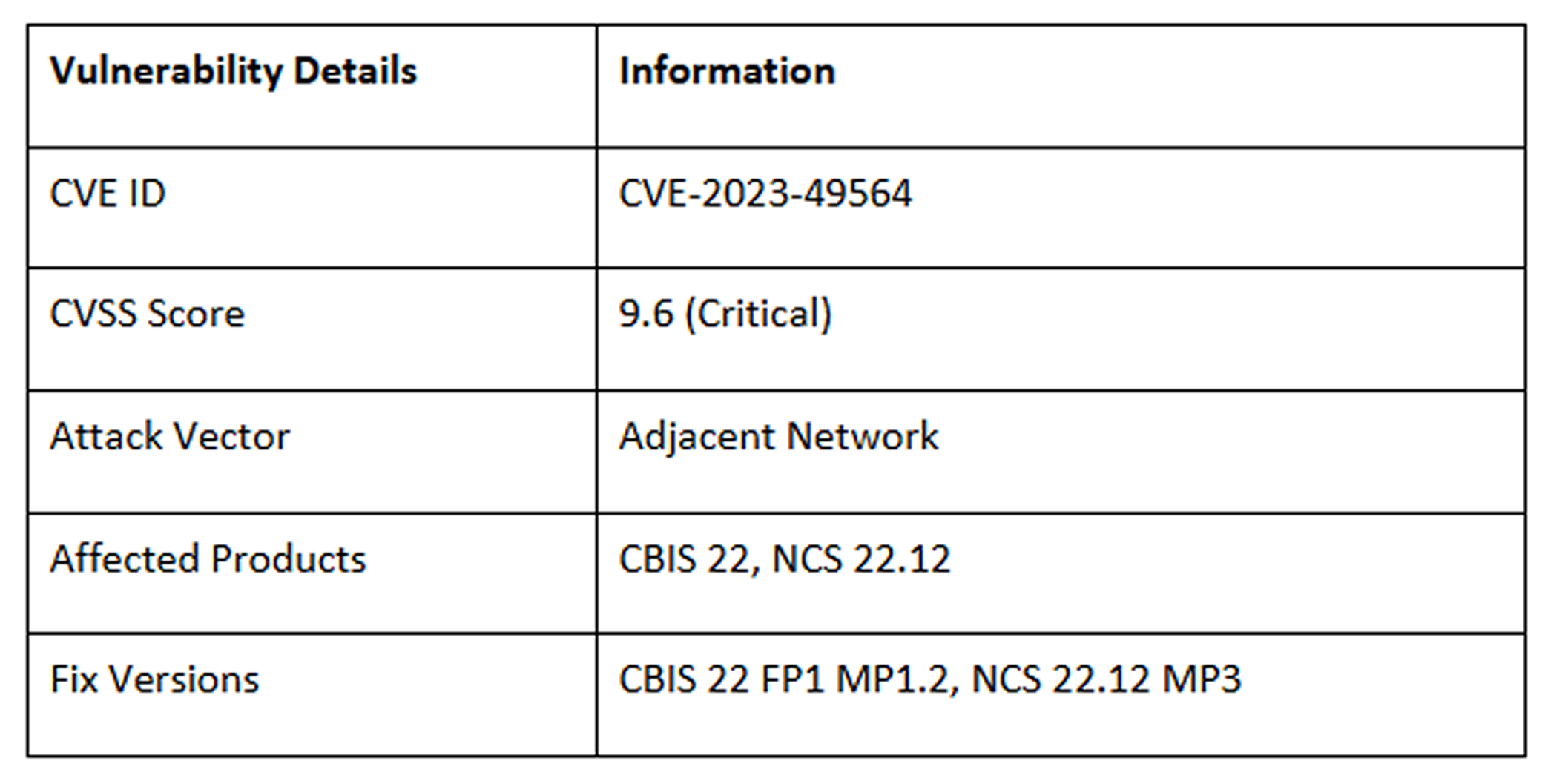
A serious vulnerability has been discovered in Nokia’s CloudBand Infrastructure Software (CBIS) and Nokia Container Service (NCS) Manager API. The flaw, tracked as CVE-2023-49564, is an authentication bypass that could allow attackers to gain full access to the system.
What the Vulnerability Does
This high-severity flaw (CVSS score of 9.6) lets an unauthorized person bypass the authentication process by using specially designed HTTP headers. This gives them complete access to restricted API endpoints without needing valid credentials.
The vulnerability affects CBIS 22 and NCS 22.12 and impacts a wide range of organizations, including businesses, service providers, and public sector agencies that use Nokia's cloud and network infrastructure.
Orange Cert researchers found the flaw, and Nokia confirmed that the root cause was a weak verification process in the Nginx Podman container that runs on the CBIS/NCS Manager host. This weakness allows attackers to manipulate HTTP headers and trick the system into thinking their requests are legitimate.
Impact and Mitigation
Exploiting this flaw requires an attacker to already have some access to the network, which is a significant concern for large enterprises. Once exploited, the vulnerability can have a major impact, allowing attackers to access sensitive data, change system settings, and disrupt network operations.
The company recommends that affected organizations apply the patches provided in CBIS 22 FP1 MP1.2 and NCS 22.12 MP3. Additionally, a partial mitigation is to restrict external firewall access to the management network.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



