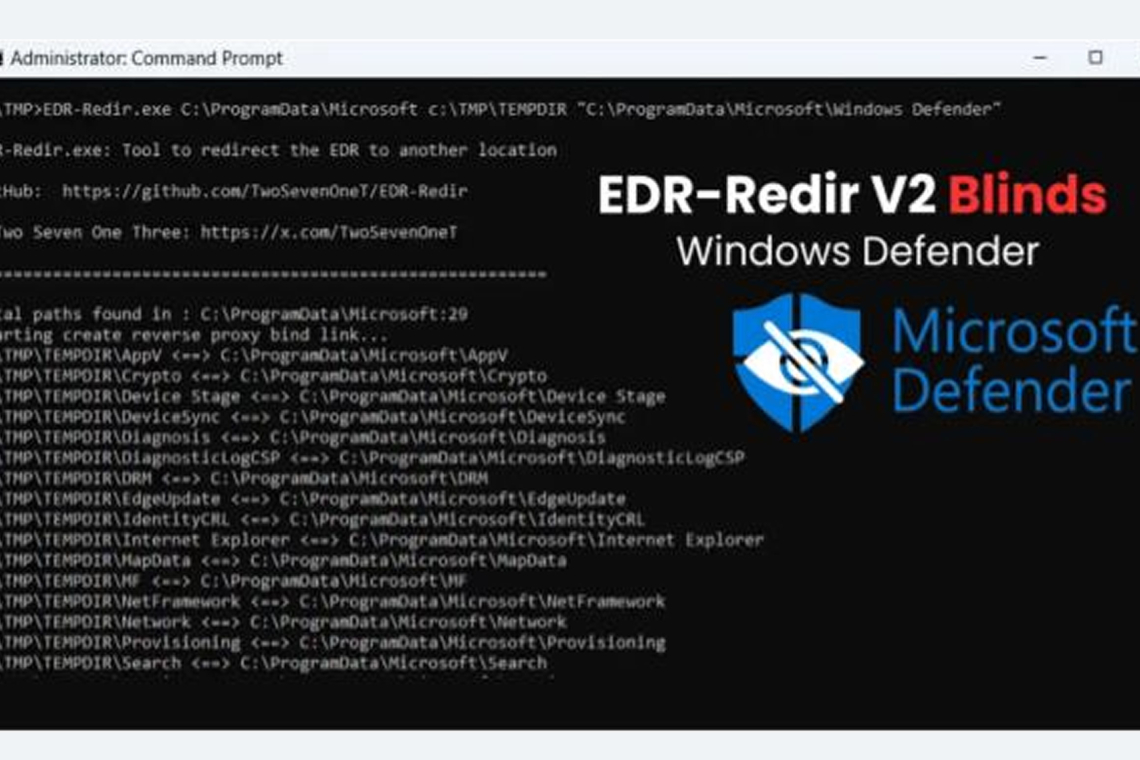
An upgraded tool called EDR-Redir V2 has been released, designed to evade Endpoint Detection and Response (EDR) systems by exploiting a novel application of the Windows bind link technology.
EDR Evasion Technique
Developed by the researcher TwoSevenOneT, this new version targets the parent directories of EDR installations such as Program Files, to create subtle redirection loops that effectively blind the security software without causing disruption to legitimate applications. Previous
versions of the tool used direct folder redirections which were often blocked. V2 bypasses this by creating a loop of subfolders that isolates the EDR's specific path for manipulation.
The tool leverages Windows’ bind link feature, which was introduced in Windows 11 24H2 and allows file system namespace redirection via the bindflt.sys driver without requiring kernel privileges. EDR solutions typically secure their own subfolders to prevent tampering, but they cannot fully restrict writes to the higher-level parent directories without breaking system installations.
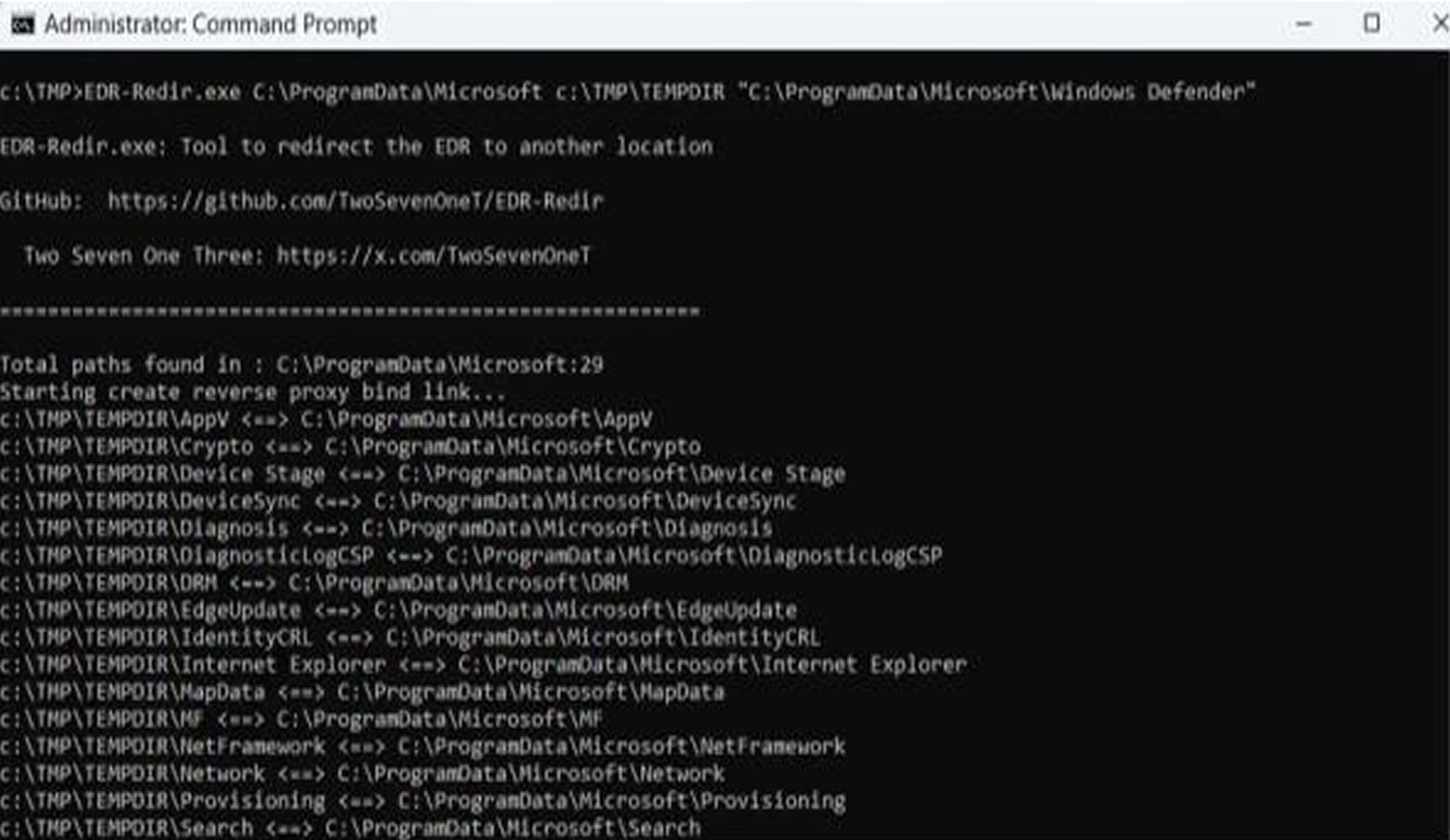
EDR-Redir V2 queries all subfolders in the parent directory, mirrors them in a controlled temporary directory (like C:\TMP\TEMPDIR), and then establishes bidirectional bind links between these mirrors and their originals. This creates loops that maintain normal access for non-EDR software. The EDR’s specific subfolder for example, Windows Defender’s path is excluded from the loop and redirected solely to the attacker’s temporary location.
Impact and Mitigation
This setup allows attackers to perform techniques like DLL hijacking or file drops in the redirected space, tricking the EDR into loading malicious components. Since developers often overlook parent-level redirections, this technique could potentially affect a wide range of EDRs. In a demonstration against Windows Defender, the tool successfully executed and
confirmed that Defender’s access attempts were rerouted through the temporary directory, effectively blinding it.
This method highlights a significant vulnerability in how EDRs protect against file system manipulations at the parent level, making folder specific safeguards ineffective. Attackers could potentially disable EDR services or inject code, operating undetected in user mode. While no widespread exploits have been reported yet, the simplicity of the method is a serious concern for enterprise environments.
Defenders should immediately begin monitoring bind link usage in critical directories like Program Files and implement integrity checks on EDR paths. EDR vendors will likely need to enhance protections for parent folders without impeding system usability.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.