An Iranian cyber espionage group, UNC1549, has been linked to a new campaign that targeted European telecommunications companies. The group successfully infiltrated 34 devices across 11 organizations, using a fake recruitment campaign on LinkedIn.
Swiss cybersecurity company PRODAFT, which tracks the group as Subtle Snail, believes it is connected to Iran’s Islamic Revolutionary Guard Corps (IRGC). The targeted companies are in Canada, France, the United Arab Emirates, the United Kingdom, and the United States.
According to a PRODAFT report, the group pretends to be HR representatives from legitimate companies to engage with employees. They then infect the victims with a MINIBIKE backdoor, which uses Azure cloud services as a proxy for its command and control (C2) communication to avoid detection.
How the Attack Unfolded
The attack involves extensive reconnaissance on platforms like LinkedIn to find key employees with high-level access, such as researchers, developers, and IT administrators.
The attackers then send spear-phishing emails to confirm email addresses and gather more information. The final and most critical phase is the fake recruitment drive. Attackers create convincing HR profiles on LinkedIn and offer nonexistent job opportunities to build trust with their targets.
If a victim shows interest, they are contacted by email to schedule an interview. They are told to click a fraudulent link that mimics legitimate companies like Telespazio or Safran Group. When they enter their information, a ZIP file is automatically downloaded.
The ZIP file contains an executable that uses DLL side-loading to run a malicious DLL called MINIBIKE. This malware then collects system information and waits for more malicious payloads, which can steal keystrokes, clipboard content, Outlook credentials, and browser data from Chrome, Brave, and Edge.
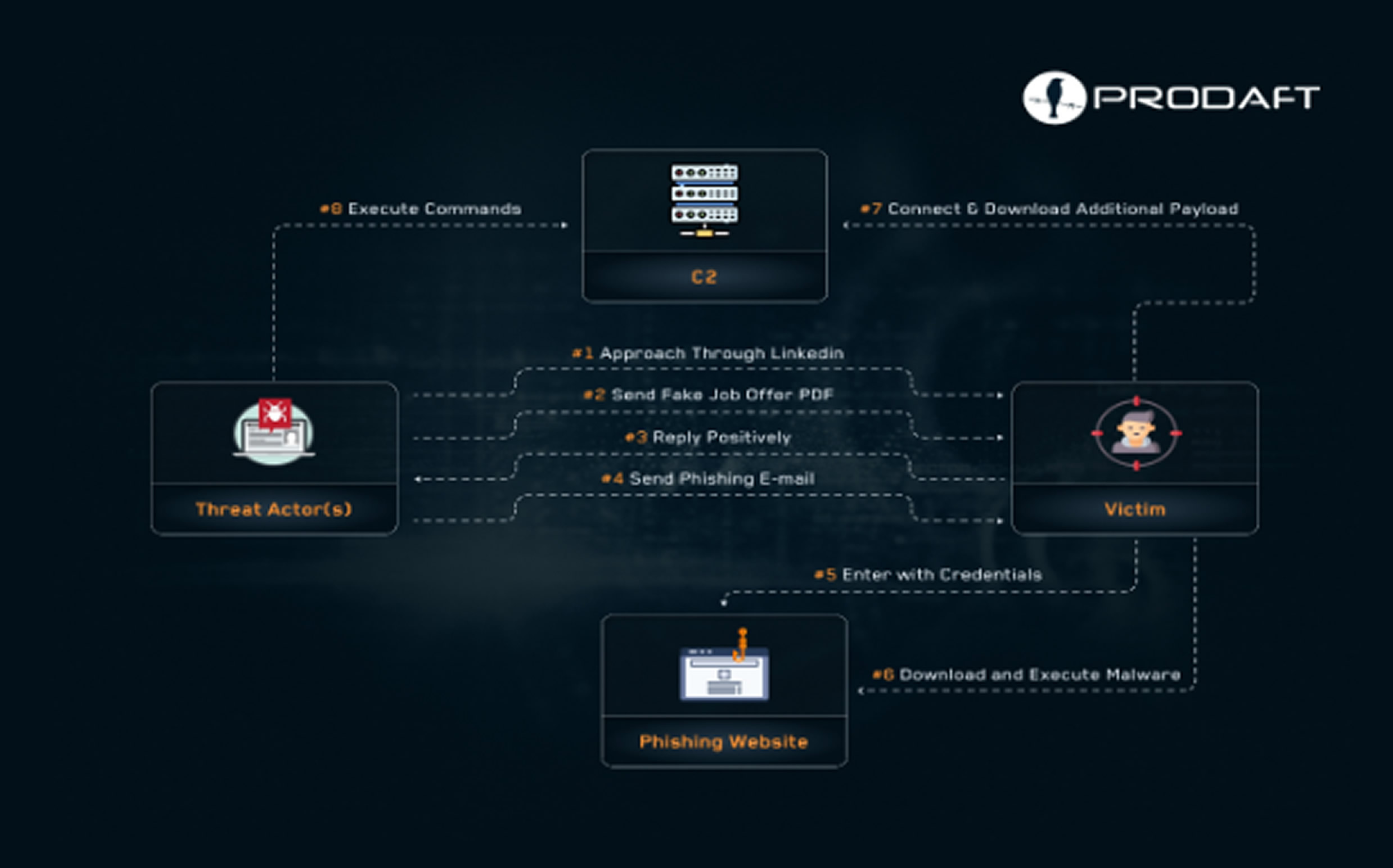
The malware is designed to be very sophisticated. It creates a unique DLL for each victim and modifies legitimate DLL files to carry out its attacks, making it hard to detect. MINIBIKE is a modular backdoor with 12 different commands for C2 communication, allowing it to list files, run processes, upload files, and execute other malicious payloads.
Stealth and Persistence
The malware uses legitimate Azure cloud services to hide its C2 traffic, making it look like normal cloud communication. It also modifies the Windows Registry so it automatically runs at startup and includes anti-analysis techniques to resist reverse engineering.
PRODAFT says Subtle Snail’s operations are very damaging because they combine intelligence gathering with long-term access to critical networks. The group actively searches for sensitive information like emails and VPN configurations to maintain control.
MuddyWater's Evolving Tactics
In a separate report, Group-IB highlighted another Iranian state-sponsored hacking group, MuddyWater, which has reduced its use of common remote monitoring tools in favor of custom backdoors.
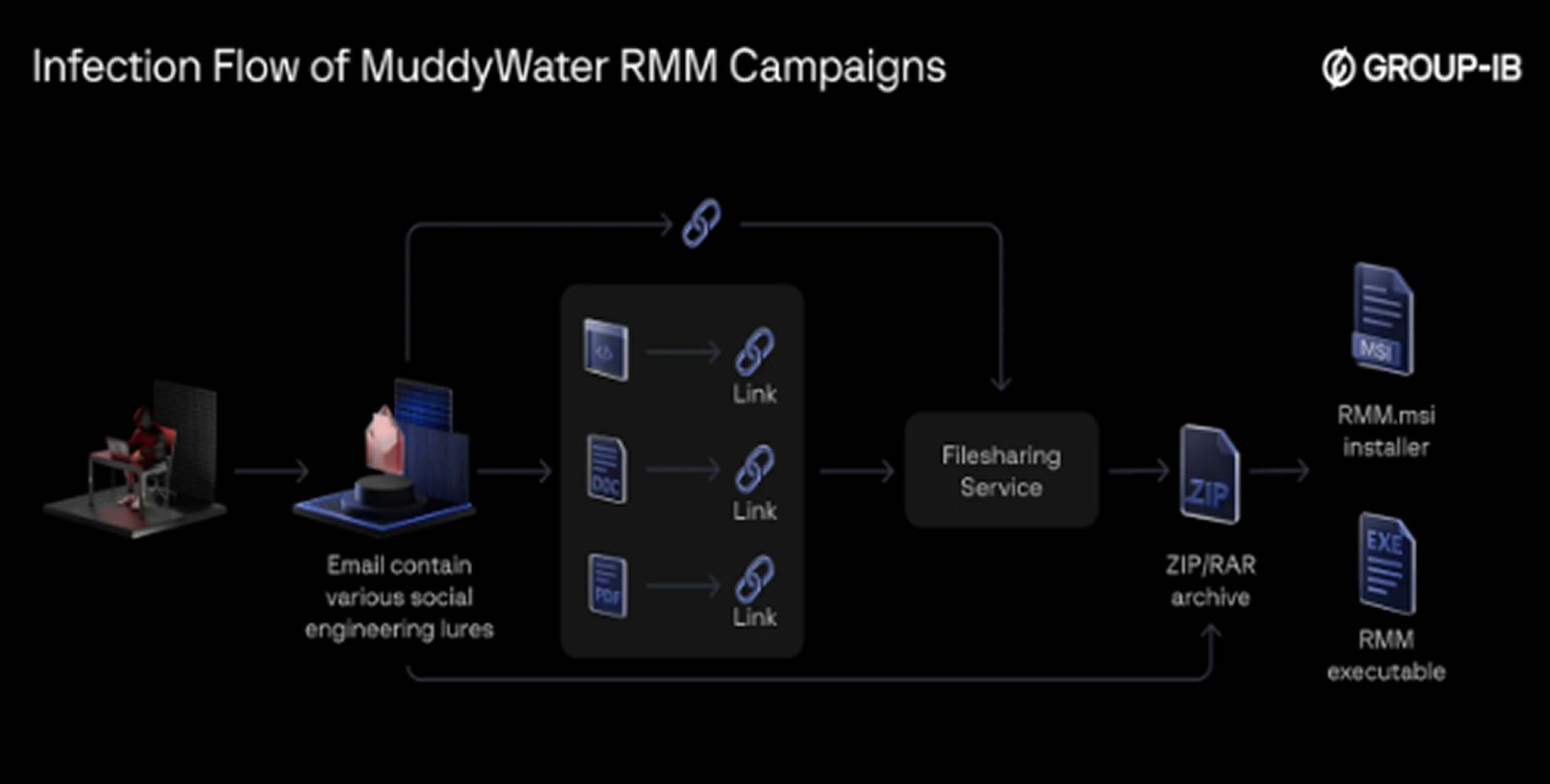
MuddyWater, believed to be a part of Iran's Ministry of Intelligence and Security, has been active since 2017. It has a history of targeting government, energy, and defense sectors in the Middle East, with recent attacks also targeting Europe and the United States.
Group-IB noted that MuddyWater still uses phishing emails with malicious attachments to infect systems and leverages services like Amazon Web Services (AWS) and Cloudflare to hide its infrastructure. Its campaigns continue to support Iranian intelligence efforts while maintaining a level of plausible deniability.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



